Network Architecture
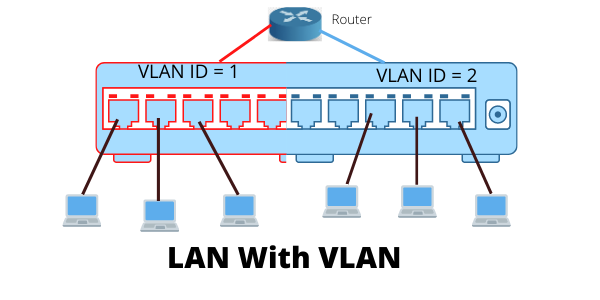
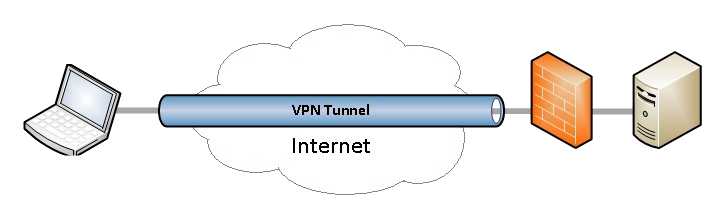
This webpage covers the overall design and purpose of my hybrid lab—managing administration, hosting web solutions, AI services, API apps, and more. It also supports ongoing learning, certification training, and hands-on experience in system administration & network engineering. My lab integrates a site-to-site VPN between my on-premise servers and AWS EC2 instances, ensuring secure communication and seamless connectivity between cloud and local environments. By combining cloud and on-premise resources, this setup enables flexible infrastructure management, allowing for seamless workload distribution and network optimization. This hybrid setup allows for advanced network simulations, penetration testing, and cloud resource management—all tailored for real-world enterprise environments.